自己搭建CodiMD的过程中;尝试了许久;才将这个应用接入到了Authing的单点登录系统中;分享一下经验;希望给有需要的人使用;如果官方可以集成为官方的模板;那么一定会锦上添花
我使用的是Authing的认证;
在线文档Codimd官方地址如下;这是一个在线协作文档的服务;对于需要协作Markdown文档的朋友们;非常有帮助。而且界面非常的简介。
CodiMD官方地址 (github.com)
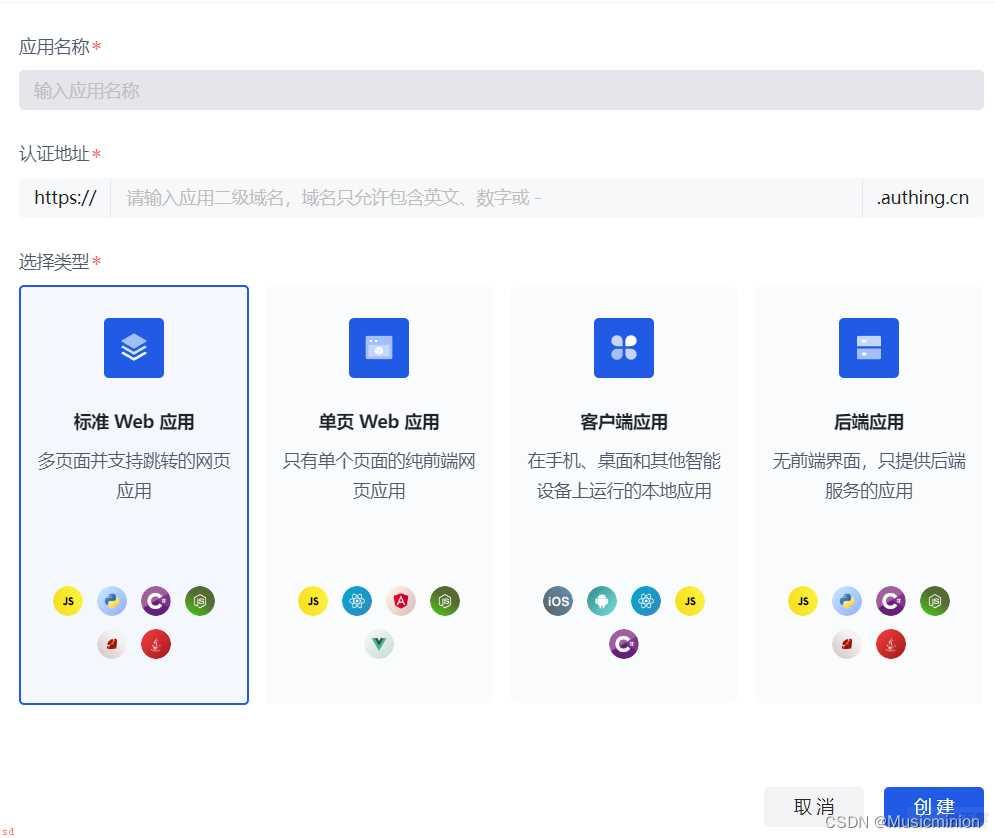
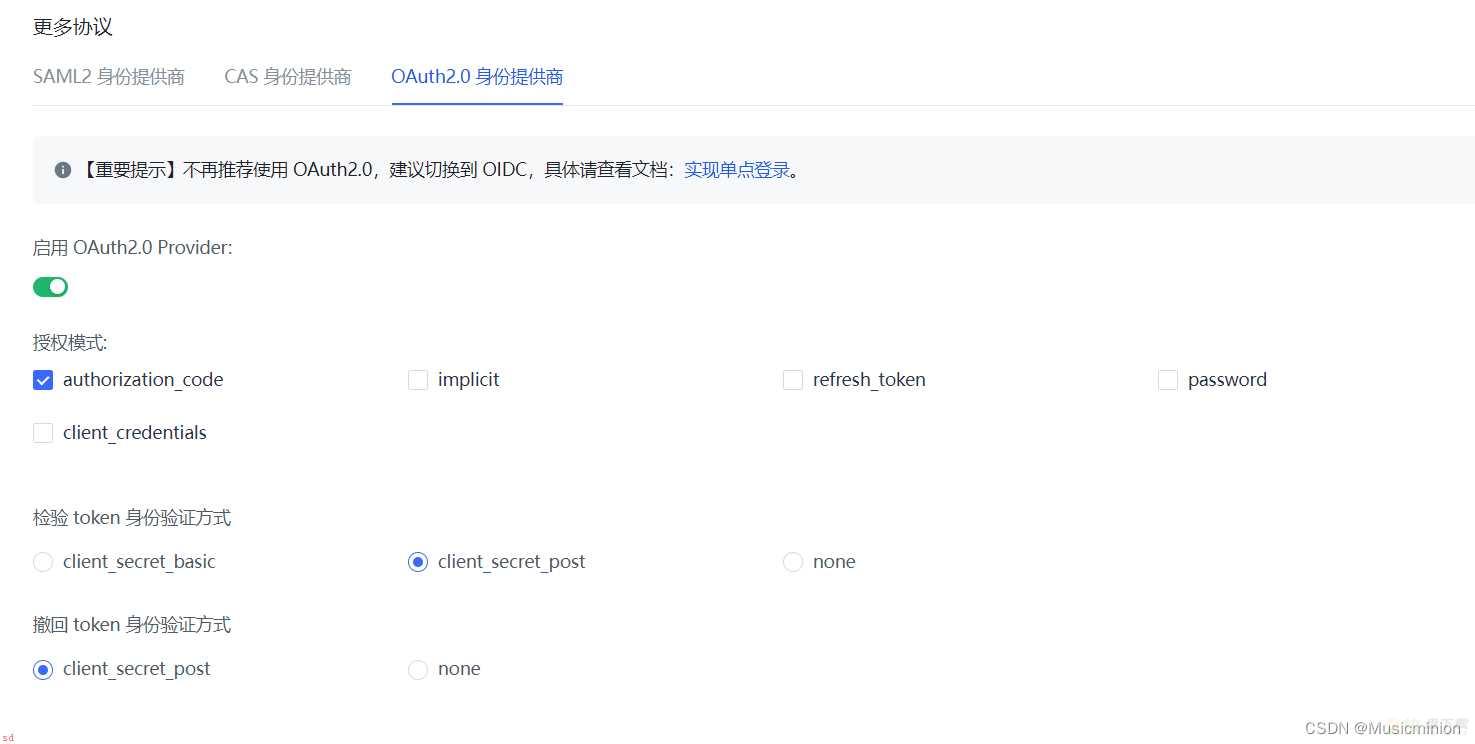
如果不懂环境变量的到文章末尾去看环境变量怎么改hhh
- CMD_OAUTH2_PROVIDERNAME=统一认证
# 显示在首页的;登录按钮的文字
- CMD_OAUTH2_CLIENT_ID=62a4**************************
# 国际惯例ClientID
- CMD_OAUTH2_CLIENT_SECRET=6e****************************
# 国际惯例SECRET_ID
- CMD_OAUTH2_BASEURL=https://********.authing.cn/oidc/
# 填写不填写;真的无所谓BASEURL;没什么用的东西
- CMD_OAUTH2_USER_PROFILE_URL=https://*******.authing.cn/oidc/me
# 重要;有人会问认证地址在哪;请回忆一下最开始的时候;你填那个webapp名字的时候就已经填写了;
- CMD_OAUTH2_AUTHORIZATION_URL=https://*******.authing.cn
- CMD_OAUTH2_TOKEN_URL=https://*******.authing.cn/oidc/token
# 特别重要;USERNAME_ATTR一定要配置成sub才行
- CMD_OAUTH2_USER_PROFILE_USERNAME_ATTR=sub
- CMD_OAUTH2_USER_PROFILE_DISPLAY_NAME_ATTR=name
- CMD_OAUTH2_USER_PROFILE_EMAIL_ATTR=email

找不到认证地址的回忆一下;

有问题就查docker的日志即可;
version: ;3;
services:
database:
image: postgres:11.6-alpine
environment:
- POSTGRES_USER=codimd
- POSTGRES_PASSWORD=I7HHOC061U71CS9
- POSTGRES_DB=codimd
volumes:
- ;database-data:/var/lib/PostgreSQL/data;
restart: always
codimd:
image: hackmdio/hackmd:2.4.1
environment:
# 下面的就是环境变量
- CMD_DB_URL=postgres://codimd:I7HHOC061U71CS9;database/codimd
- CMD_USECDN=false
- CMD_GITHUB_CLIENTID=219ba1be6c66b0d97f23
- CMD_GITHUB_CLIENTSECRET=9fab2213486135d8ec510a643b4afa2cd8988803
# 上面的就是环境变量
# 注释;就是那种简单的key value的格式
depends_on:
- database
ports:
- ;51014:3000;
volumes:
- upload-data:/home/hackmd/app/public/uploads
restart: always
volumes:
database-data: {}
upload-data: {}
把Codimd的官方文档的链接放上来;由于一般打不开;所以我把原文也放在这里面了;给有需要的同志们参考一下;
Generic OAuth 2.0 - HackMD
CodiMD can integrate any OAuth 2.0 provider via generic oauth 2.0 provider .
Before setup OAuth 2.0 provider, you need to contact your OAuth 2.0 service to request some parameter described below.
the authorization url for OAuth 2.0 service