实验目的:
配置公司总部到公司分部的IPSEC VPN,实现网络的连通。
实验拓扑:
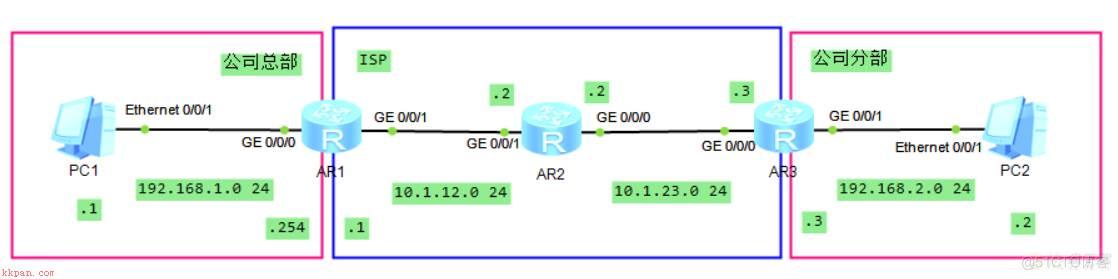
一、基础配置:
1.配置好各个设备的IP地址。
2.设置R1/R3各有一条默认路由通往R2。
3.先测试R1是否能ping通R3,ping通后才可做IPSEC VPN的配置。
4.保存基本配置,save。
二、IPSEC VPN配置:
[R1]ipsec proposal ipsec
Display ipsec proposal name ipsec
R3必须配相同的配置,这里不更改参数。
[R3]ipsec proposal ipsec
//可更改选项:
Encapsulation-mode tunnel-封装模式
Esp authentication-algorithm ?-认证方法
Esp encryption-algorithm ?-加密算法
配置访问控制列表:
[R1]acl 3000
Rule permit ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
[R3]acl 3000
Rule permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
配置IPSEC的策略-手动配置模式:
R1
[R1]ipsec policy yeslab 10 manual
Tunnel local 10.1.12.1
Tunnel remote 10.1.23.3
Security acl 3000
Proposal ipsec
Sa spi inbound esp 12345
Sa spi outbound esp 54321
Sa string-key inbound esp cipher huawei@123
Sa string-key outbound esp cipher huawei@123
Int g0/0/1
Ipsec policy yeslab
R3
[R3]ipsec policy yeslab 10 manual
Tunnel local 10.1.23.3
Tunnel remote 10.1.12.1
Security acl 3000
Proposal ipsec
Sa spi inbound esp 54321
Sa spi outbound esp 12345
Sa string-key inbound esp cipher huawei@123
Sa string-key outbound esp cipher huawei@123
Int g0/0/0
Ipsec policy yeslab
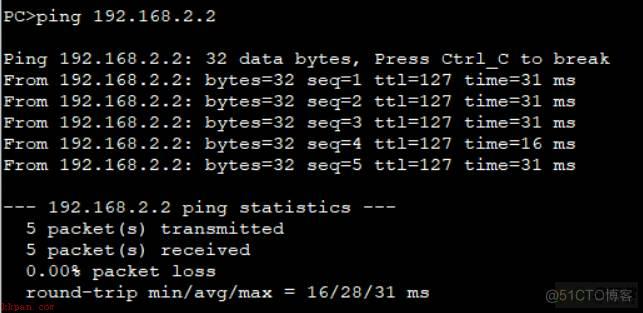
PC1pingPC2,此时可以ping通。
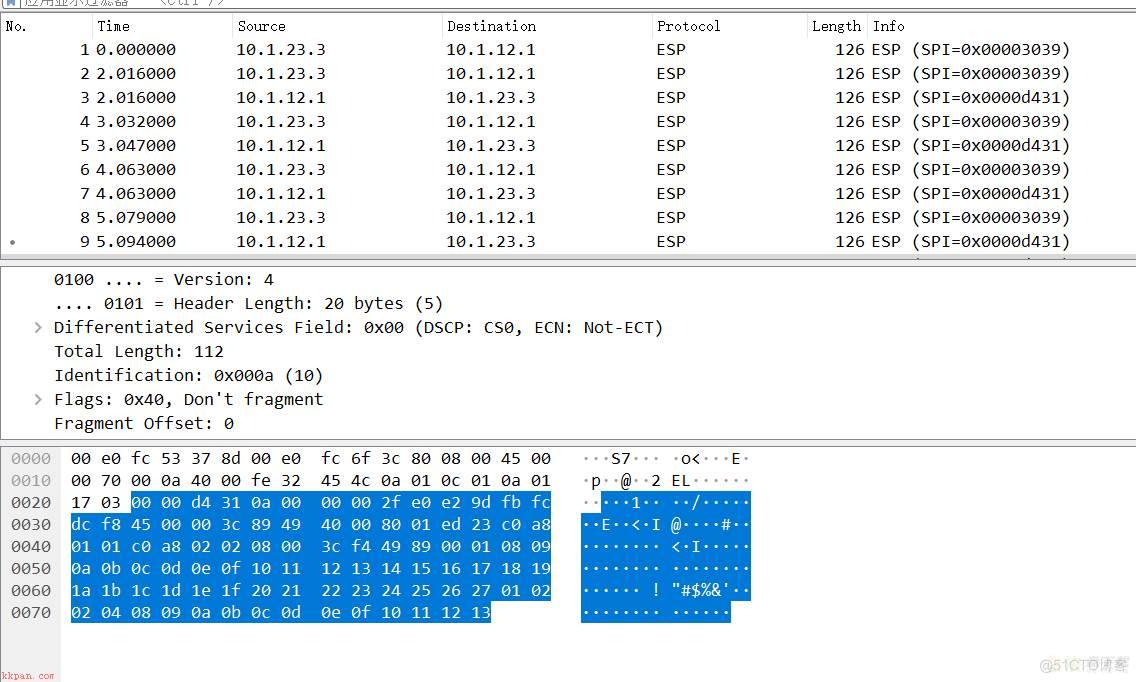
在R1上的g0/0/1接口进行抓包,发现数据都被加密了。
手动配置模式完成。
_____________________________________________________________________________
配置IPSEC的策略-动态配置模式:
先去掉2个出口路由器的接口策略应用:
[R1]]int g0/0/1
Undo ipsec policy
[R3]]int g0/0/0
Undo ipsec policy
R1
[R1]ike proposal 10
Display ike proposal number 10
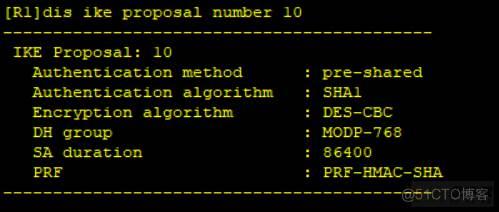
q
[R1]Ike peer to_R3 V1
Remote-addresss 10.1.23.3
Ike-proposal 10
Pre-shared-key cipher huawei@123
q
Ipsec proposal hcie
q
Ipsec policy hcie 10 isakmp
Secutrity acl 3000
Ike-peer to_R3
Proposal hcie
q
Int g0/0/1
Ipsec policy hcie
R3
[R3]Ike proposal 10
q
Ike peer to_R1 V1
Remote-addresss 10.1.12.1
Ike-proposal 10
Pre-shared-key cipher huawei@123
q
Ipsec proposal hcie
Display ipsec proposal hcie
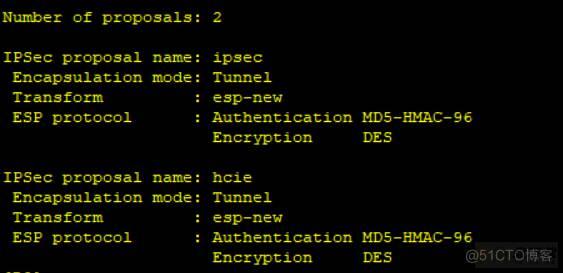
q
Ipsec policy hcie 10 isakmp
Secutrity acl 3000
Ike-peer to Proposal hcie
q
Int g0/0/0
Ipsec policy hcie
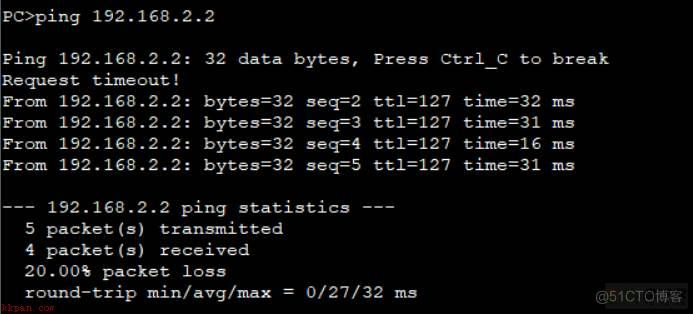
PC1pingPC2,此时可以ping通。
在R1上的g0/0/1接口进行抓包
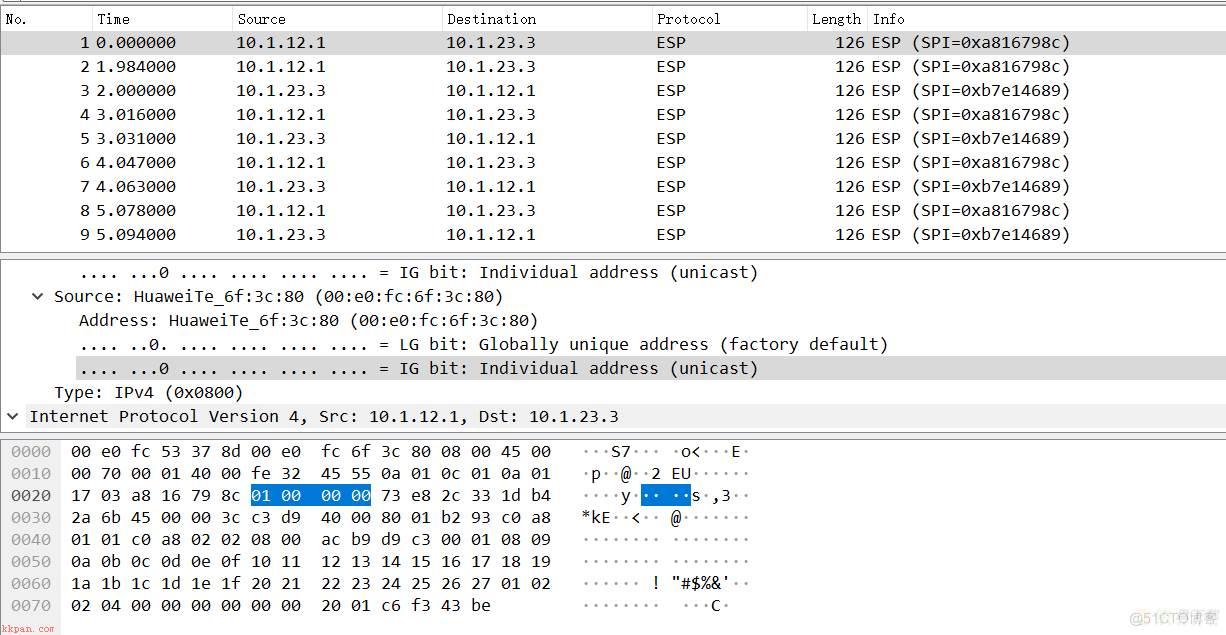
动态模式配置完成。